At present, blockchain application builders often face the difficulty of choice and need to make a lot of trade-offs and development work to achieve their desired product form. The development cost of the underlying blockchain is relatively high. Developers usually need to perform secondary development based on a suitable underlying chain and make adaptive modifications to their applications to adapt to the characteristics of the underlying chain. At the same time, due to the contradictions between the three points of safety, efficiency, and fairness, it is impossible to achieve the optimal at the same time. There is no perfect blockchain bottom layer that can adapt to all scenarios.
For example, a public chain project that selects PoW as a consensus algorithm has to sacrifice throughput and transaction confirmation speed while ensuring that a large number of nodes participate in the consensus and reach 50% fault tolerance, which is difficult to meet real-time application requirements and consumes a lot of power; Selecting a directed acyclic graph (DAG) as the consensus-based project, although ensuring decentralization and gaining throughput advantages, it does not solve the problems of high energy consumption and slow transaction confirmation; selecting Hyperledger Fabric as the project of the underlying chain, you can Satisfy the needs of high throughput, fast confirmation, and low energy consumption, but introduces dependence on centralized nodes.
One problem that needs to be pointed out is that development on different platforms is often not reusable, and the efforts made on a certain platform usually cannot be directly migrated to another platform. Compared with the specific realization of business functions, the initial stage The choice becomes particularly important. The above-mentioned problems are also known as platform “lock-in†risks. Blockchain application developers have to choose a specific underlying blockchain technology at the beginning. And it will be restricted to a certain extent in the future.
Zhigui Blockchain is committed to providing underlying blockchain services that are suitable for a variety of business needs, in order to ensure that the underlying development maintains its ideal underlying technology stack. Fang makes the upper-level application development of the blockchain. The underlying platform of the paper precious blockchain is versatile and modular. Playability and security are the design principles, making the construction of the underlying blockchain as lightweight as possible. At the bottom of the organization, each consensus module and functional module can be customized and pluggable, providing benefits for adapting to specific scenarios.
Design Principles
Principle of functional decoupling
Between the various modules, especially the services between different functional layers, functional decoupling should be achieved as much as possible. For example, the task of the underlying module is to build a decentralized system that is secure and meets the consistency requirements. It should not worry about how users use their own private keys; blockchain applications should deal with specific business logic more, and Functions such as interface adaptation, account management, and blockchain information query are handed over to other specialized modules for processing, thereby effectively avoiding problems such as over-complex architecture, wrong coupling, and difficulty in debugging.
Compatibility principle
The basic modules of the blockchain should follow the compatibility principle in design, so that different application developers can integrate quickly and easily. For example, the content of data transmission should use common standards to facilitate users' understanding; the account system should meet the needs of most scenarios, and content such as personal information and role information should not be added.
Pluggable principle
When the compatibility principle cannot be met and different modules must be used to provide the same type of function, the pluggability principle should be considered. For example, it should be possible to switch between different consensus engines, and users can combine specific functional modules according to their own needs to meet specific functional or performance requirements.
Security principle
The design of the bottom layer and application of the blockchain should follow the principle of safety first. Ensure the interests of users, so that the system can remain robust even when subjected to a certain degree of malicious attacks. This is particularly important in the bottom layer and applications of blockchains without a centralized management system.
Underlying chain architecture
The underlying chain is the cornerstone of the blockchain system and provides support for the distributed consensus of information on the chain. The underlying general architecture of the paper expensive blockchain products is shown in the following figure:
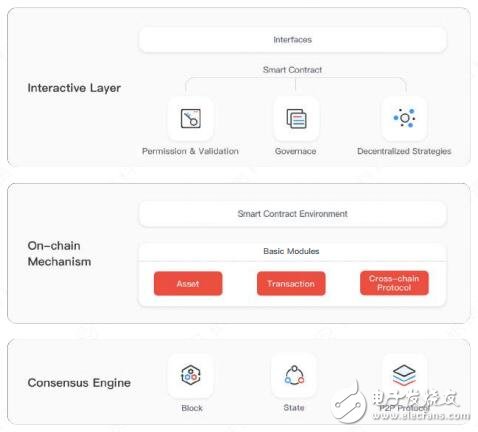
Consensus engine-Consensus engine is the operating foundation of the underlying chain. Among them, the block and state are the consensus content reached by the consensus agreement between distributed nodes, and are the basic data storage of the blockchain operating mechanism; the P2P network protocol is the basic protocol for self-organization and communication between nodes. These two modules work together to lay the foundation for the operation of the blockchain system.
System on the chain-The system on the chain is the functional core of the underlying chain. This part includes a series of pluggable underlying basic logic closely integrated with the consensus mechanism. This part includes basic cryptographic algorithms for distributed entity identification and authentication, on-chain assets, transactions, cross-chain protocols, etc. A cross-chain protocol is an interaction method followed by the interaction and connection of assets between chains and the transmission and circulation of information. In addition, the smart contract operating environment (such as EVM, JVM, x86VM, and Docker, etc.) provides a suitable environment for supporting the normal and orderly execution of smart contracts.
Off-chain interaction-Off-chain interaction is the external window of the underlying chain, including smart contracts and interactive interfaces. The user can install, delete, initialize, freeze and other operations on the contract, or interact with the smart contract through the interface to achieve the required distributed business logic, or to review the contract request, user identity, and the status of other contracts. Blockchain for governance and so on.
1. Consensus engine
The consensus engine is the operating foundation of the blockchain distributed system, and its core function is to sequence transactions in the blockchain network.
Blocks and state machines
The blockchain network is a distributed system composed of multiple nodes. The state machines of blocks and nodes together constitute the bottom layer of the system. Among them, the block stores the historical records of all operations that require consensus in the system (such as transactions). The records of these operations are extremely difficult to be tampered with; the state machine of the node stores the latest state of the node when it is running, and it is the underlying maintenance of the blockchain. State storage space, which enables smart contracts to be executed correctly.
If the block is compared to the "hard disk" of the blockchain, then the state machine is the "memory" of each running node of the blockchain. The record of each operation is recorded in the block, and the current state of the block chain is obtained through the sequential playback of the entire chain. This separate design makes it possible to run smart contracts. Otherwise, the blockchain will need to replay transactions in all blocks to obtain the user's current balance, which is difficult to be practical in scenarios where there are a large number of transactions. Since the state machine is stored on each node separately, the state machine of a single node machine may be tampered with, but the node whose state has been tampered with cannot reach a consensus with other nodes, thus being isolated by the entire network.
Consensus algorithm
Each node's agreement on the block and state needs to be guaranteed by the consensus algorithm. The choice of consensus algorithm is often restricted by the specific application environment and application purpose. For example, when the blockchain system is used for collaboration between relatively independent business departments in the company, CFT (Crash Fault Tolerance) consensus algorithms can be selected, which is more conducive to improving business efficiency and reducing the cost of mutual trust and consensus among business departments ; When the blockchain system is used for consensus among alliance members, you can choose PBFT (PracticalByzanTIne Fault Tolerance), Tendermint and other consensus algorithms that can defend against certain malicious nodes while taking into account processing efficiency; when the blockchain system is exposed to the public When the network is free for everyone to access, it may be necessary to choose PoW (Proof of Work), PoS (Proof of Stake), etc., which can accommodate a large number of users, tolerate less than 50% of malicious nodes, and safely maintain distributed ledger algorithms. These algorithms have their own advantages and disadvantages, and they are difficult to replace each other. Only when facing specific business scenarios can a truly suitable algorithm be designed.
In response to this problem, the paper expensive blockchain adopts a pluggable consensus engine, encapsulates the consensus algorithm with a unified interface, and separates the upper-level business logic from the lower-level consensus unit. For different consensus methods, develop according to the same consensus interface, which can realize the upper-level modules compatible with the paper expensive blockchain, realize the decoupling of business logic and the consensus engine, and replace different types of consensus algorithms according to the needs of different scenarios. .
2. On-chain system
The system on the chain includes the core processing mechanism of the node, which realizes some business functions closely related to the blockchain consensus in a decentralized scenario, and some of the mechanisms can be provided to developers for the development of upper-level applications. These mechanisms work together with the consensus engine to complete the basic functions of the underlying chain.
Fundamental methods of cryptography
Blockchain is also called "System of Proof", and the basic methods of cryptography are powerful tools to support proof. It provides the possibility for the realization of various decentralized functions, and it is also the most basic algorithm library and toolkit for the realization of distributed strategies. Algorithm packages mainly include, but are not limited to, the following open source, theoretically deduced and experimentally verified cryptographic libraries.
Hash algorithm
The hash algorithm ensures the integrity of the information through a one-way hash function to prevent the information from being tampered with. Hashing algorithms are used in scenarios such as the realization of the chain structure between blocks, the hashing of the information to be signed before signing, and the generation of a unique ID on the chain.
Asymmetric encryption and digital signature algorithm
Asymmetric encryption mainly provides digital signature and verification functions in the underlying system of the blockchain. The signature verification work exists in the entire transaction process, involving every node in the middle, such as submitting and verifying transaction requests, submitting and verifying endorsement signatures, submitting and verifying block signatures, etc. Asset transactions conducted in the anonymous account address system generated and managed by users will also involve asymmetric encryption and digital signatures. In consideration of the security of the private key of the user account, the paper responsibility proposes a secure hardware private key storage scheme that complies with the ISO 7816 standard to ensure the user chain. The safety of the assets on the market.
Ring signature algorithm
Zhigui provides a ring signature algorithm module. Meet the needs of users for transaction anonymity. Under normal circumstances, a general encryption signature can track the transaction and obtain the sender's public key and address. By calling the paper expensive ring signature module, it is possible to realize that for any transaction, it is impossible to track who the payer is; for the two transactions sent out, other people cannot prove whether they are sent to the same payee.
Homomorphic encryption
When users receive data services, they need to send the data in plain text to the data service provider. In scenarios where data privacy is emphasized, how to enable users to obtain data services while ensuring the confidentiality of user data is very important. Paper Responsibility can ensure the confidentiality of user data throughout the service process by providing homomorphic encryption components. The user sends the data in cipher text to the data service provider. The data service performs a specific form of algebraic operation on the ciphertext, and the result is still encrypted; after the user obtains the encrypted result, the result obtained by decrypting it is the same as the result obtained by performing the same operation on the plaintext. Zhigui Technology currently supports encryption algorithms that satisfy additive homomorphism and multiplicative homomorphism, and will further support multi-key fully homomorphic encryption schemes based on perturbed learning in the future.
Accounts and transactions
Accounts and transactions are digital asset models that are directly guaranteed by cryptographic methods, and they are also the basic elements to realize the on-chain incentive mechanism. It ensures that the blockchain can become a self-organizing and self-driven decentralized system. For any account asset system, the core issue is security, followed by performance.
Security is the most basic and most important requirement of the account system. First of all, due to the transparency of the blockchain ledger, all consensus nodes need to confirm transactions and reach a consensus. The traditional cryptographic account system cannot support distributed applications on the blockchain. In this scenario, a decentralized account system that relies on cryptographic algorithms such as asymmetric encryption has emerged, and blockchain applications can ensure everyone's asset ownership in an open environment. Secondly, because the ledger on the blockchain allows anyone to access it, malicious operations are difficult to control and roll back, and it is necessary to ensure that no one can do evil from the mechanism. One of the most typical points is that the decentralized account system should ensure that it can resist Double Spending Attack. For example, Bitcoin uses the Unspent TransacTIon Output mechanism to ensure that the outflow of funds in the flow of funds is always equal to the inflow; Ethereum uses Nonce to ensure that transactions will not be replayed. Regardless of the scheme adopted, ensuring the security of the account’s assets and resisting any possible attacks are the most basic requirements of the blockchain account system.
Since the account system is closely related to payment, a decentralized account system should also support high concurrent transactions. There are two bottlenecks in transactions in the decentralized account system. First, all transactions must go through a distributed consensus, and the consensus process takes time; second, the account status of the blockchain account is modified according to the confirmation of each block, if a transaction is based on the account status of the current block It is constructed and broadcast to the blockchain network after the next block arrives. During this period, the account status is likely to have changed, resulting in conflicts. The decentralized account system should be able to correctly and effectively handle these two issues, support high concurrent transactions, and thus be able to obtain a wider range of applications.
Smart contract operating environment
Smart contracts have special distributed characteristics, and their operations and available resources should ensure that they cannot cause any damage to the host. In order to ensure that the smart contract can be executed correctly under resource-constrained conditions, the smart contract virtual machine is an indispensable basic operating environment. By providing a limited instruction set and special resource scheduling strategy, it ensures that the execution of smart contracts will not cause harmful consequences to the underlying chain.
Common smart contract operating environments include Ethereum's Ethereum Virtual Machine (Ethereum Virtual Machine), Fabric's Docker, etc. There are also virtual machines that rely on specific hardware or implement special algorithms, which can be customized according to the needs of the application.
3. Off-chain interaction
The off-chain interaction layer is the window through which the blockchain communicates with the outside world, and is composed of smart contracts and their external interfaces.
Smart contracts are an important carrier for blockchain application developers to communicate with on-chain mechanisms to realize decentralized business logic, and it is also the basis for the prosperity of blockchain ecology. Through smart contracts, engineers can build credible applications in the decentralized environment of the blockchain and realize business logic with distributed consensus characteristics. Every line of code they write, and every input and output of the program, will be faithfully recorded and evidenced by the underlying blockchain. These smart contracts can be divided into three categories according to their functions: The first category is protection mechanisms such as authorization authentication and correctness checking that exist in the process of off-chain interaction. Through these mechanisms, a permission chain with authority management can be constructed, which has a wide range of applications in many restricted scenarios; the second type is on-chain governance contracts. These contracts will provide on-chain auditing, contract management and other functions, and all operations will be recorded on-chain; the third type is business contracts, these contracts, together with off-chain systems, constitute a variety of decentralized applications . All smart contracts must comply with the interface development specifications, and implement the calling interface in accordance with the requirements of the external interaction protocol to provide services to the outside world.
The developers of smart contracts seem to be dancing in chains. On the one hand, in order to achieve decentralized applications, they must follow the restrictions proposed by the on-chain mechanism and use limited operation methods and limited computing resources to process information on the chain; they are prohibited from using random numbers, etc., which will affect Mechanism for reaching consensus; they must ensure that their code is error-free. On the other hand, contract engineers should design contract functions and application structures from a comprehensive and systematic perspective in response to the various requirements put forward by external systems, and finally adapt and deliver the external interaction layer for use by external applications. Smart contract engineers must be rigorous in logic and rigorous code. They are not only familiar with the basic principles of computers and the flexible application of algorithms, but also familiar with the running logic of distributed systems and the architecture design of application systems. This provides a very high level of technology for application developers. Claim.
Application architecture
For a complete blockchain application, the application architecture of the paper expensive blockchain is shown in the following figure:
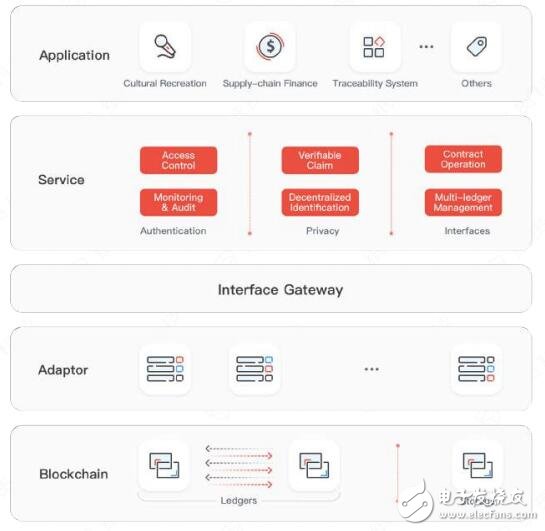
Among them, the bottom layer of the blockchain cooperates with the storage module to meet the needs of most business scenarios; the blockchain adapter is a converter that adapts and unifies the interfaces of different bottom layers under the same protocol framework, and is backward compatible with different bottom layers. , Provide a unified interface upwards, which greatly saves the integrated development cost of upper-level business services; the interface gateway is a unified interactive entry for request forwarding. The auxiliary module of load balancing also isolates malicious attacks. The firewall that records the problem operation; the blockchain service is a simplified operation form provided to the outside through the abstraction and encapsulation of the underlying interface of the blockchain, and the infrastructure for user management, identification and verification for the upper-level applications as needed; through The customized scheduling and packaging of blockchain services are finally integrated into blockchain applications for users to use.
1. Blockchain adapter
Blockchain adapter enables most of the functions of the upper-layer application to focus on the development of application logic without caring about the specific protocol of the underlying chain.
Blockchain adapter is a key module that decouples the bottom layer from the application. As pointed out in the explanation of the off-chain interaction layer of the underlying chain. The developers at the bottom pay more attention to the underlying processing performance, interface efficiency and other indicators. They don't want to be bound by the application, while the application developers pay more attention to the realization of business logic. They don't want to be "locked" by the specific platform. In order to meet the needs of both parties, the existence of a blockchain adapter is essential.
The blockchain orchestrator can unify the off-chain interaction interfaces of different chains under the same protocol, so that application developers can build applications in the same framework. With the help of the blockchain adapter, developers can start developing on a new platform without changing their thinking; they only need to pay a small learning cost to read the extension method of a specific chain, and then they can Conveniently integrate the special functions of the chain.
2. Service middleware
Service middleware is a basic functional module in the form of an "extension package", which completes the specific realization of a fine-grained service.
For example, when an application developer wants to complete a certain decentralized asset management function, he only needs to introduce the blockchain interactive middleware, and provide the application side with interfaces such as transaction query, account query, transaction initiation, etc., namely Can concentrate on developing the specific functions of the client.
When an application developer wants to complete the function of distributed data management, he needs to introduce storage management middleware and blockchain interaction middleware, and provide functions such as data management and data summary on the application side to support Realize the function of decentralized data on-chain and storage.
The above-mentioned service middleware will be provided to developers in the form of broadcasts and independent projects in the early stage, and will exist in the form of an application mall in the later stage. Service middleware can greatly accelerate the development of blockchain applications, and it is also the basis for the prosperity of the development system.
3. Blockchain application
Blockchain application refers to an application instance based on blockchain development. It is a service that directly faces users and provides functions. Provide support for people to use blockchain. Common blockchain applications include blockchain browsers, blockchain depository services, blockchain asset management tools, and so on. Since the birth of blockchain, these applications have played a huge role in the use and popularization of blockchain, and some applications have even become the standard configuration of blockchain projects.
In the relationship with service middleware, there is no strict boundary between the two. When the application developer thinks that the time is right, he can package his application or part of it into service middleware. For other application developers to use; developers can also encapsulate different service middleware to achieve specific blockchain applications.
In the process of exploring the blockchain, Zhigui Technology has also accumulated a series of blockchain applications, and will continue to serve users or give back to the community in the form of industry applications or service middleware.
A tablet computer is an electronic device that integrates mobile commerce, mobile communication and mobile entertainment, with a touch recognition LCD screen, handwriting recognition and wireless network communication functions. At present, the tablet computer has become the most popular electronic product.
1.In appearance, the tablet computer looks like a large-screen mobile phone, or more like a separate LCD screen.
2.In terms of hardware configuration, a tablet computer has all the hardware devices of a traditional computer, and has its own unique operating system, compatible with a variety of applications, and has a complete set of computer functions.
3.Tablet PC is a kind of miniaturized computer. Compared with traditional desktop computers, tablet computers are mobile and flexible. Compared with notebook computers, tablet computers are more compact and more portable.
4.Tablet PC is a digital notebook with digital ink function. In daily use, you can use the tablet computer like an ordinary notebook, take notes anytime and anywhere, and leave your own notes in electronic texts and documents.
Tablet Pc Pad,Mobile Tablet,Scratch Pad Tablet Pc,Tablet Pc,Tablets & Presentation Equipment,Educational Tablet
Jingjiang Gisen Technology Co.,Ltd , https://www.gisentech.com