In recent years, chaotic secrecy and its application have become a research focus in the field of information security, especially the problem of chaotic digital image, voice and video encryption has attracted great attention of researchers. However, the current research on chaotic secrecy is mainly limited to the encryption of digital images and speech, but there are very few studies on video encryption. Traditional encryption algorithms such as DES, IDEA, Blowfish, RSA, etc. can theoretically be used for digital video encryption. However, the above method does not take into account the characteristics of the video file, which will inevitably lead to the destruction of the structure of the file, and because of the massive nature of the video file, the rate of encryption of the above algorithm cannot be guaranteed. Therefore, it is necessary to study new video encryption algorithms with high security and fast encryption speed [5-13].
This article refers to the address: http://
This paper proposes the use of three-dimensional Lorenz chaotic system and Matlab simulation tools to achieve chaotic digital video encryption. The Matlab tool is used to generate the AVI video signal. At the same time, using the chaotic sequence to be very sensitive to the initial conditions and system parameters, the responsive algorithm is used to encrypt and decrypt the generated AVI video, and finally the chaotic sequence is initialized. The conditions and system parameters are adjusted weakly, and the simulation results are analyzed in depth.
1 AVI video file structure features
Audio Video Interleaved (AVI) is a file format that combines voice and video. It uses a lossy compression method for video files, but the compression is relatively high. AVI supports 256 colors and RLE compression. An AVI file can contain multiple different types of media streams. It stores video information in a series of bitmaps. And add digital video information stored in digital form to the file.
AVI consists of three parts: a file header, a data block, and an index block. The file header includes general information of the file, and defines parameters such as a data format and a compression algorithm. The data block contains the actual data stream, ie the image and sound sequence data, which is the main part of the file and the main part that determines the file size. The size of the video file is equal to the data rate of the file multiplied by the length of time the video was played. The index block includes a list of data blocks and their location in the file to provide random access to data within the file.
2 Lorenz chaotic system and discretization
Using a Lorenz chaotic system for encryption and decryption of AVI video files, the mathematical expression of the dimensionless equation of state for the Lorenz system is [14]:

According to equations (1) and (2) and the above parameters, the numerical simulation results of the attractors in the Lorenz chaotic system can be obtained. Figure 1 shows the attractor phase diagram of the Lorenz chaotic system in the xy direction.
3 Design of video encryption algorithm based on Lorenz chaotic system
3.1 Reading of AVI video files
Chaotic encryption is performed by randomly sampling a piece of AVI video. Since Matlab only supports AVI video files of ZJmedia Umcompress RGB24 encoding mode, it is necessary to convert the collected video files to make them unobstructed. Go to the Matlab tool. Using the professional conversion software Winavi to operate, the video is processed into the Matlab tool after corresponding processing. 3.2 Video Encryption Scheme
According to the principle of cryptography, the video information must first be scrambled, and then the chaotic system is used for diffusion encryption.
The chaotic system state equation of equation (2) is used to realize digital video chaotic encryption after discretization. On the basis of driving the responsive synchronization, a closed loop and feedback are formed after the signal is added, so that the driving system and the response system have synchronization signals, and the working principle is as shown in FIG. 2 .
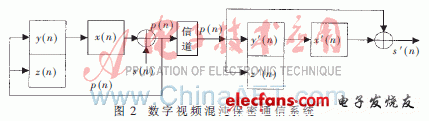

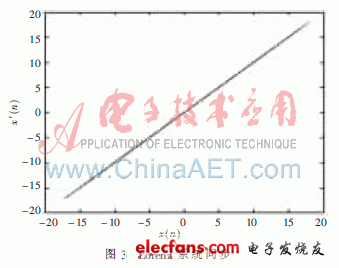
It can be obtained by programming after programming on Matlab software. The Lorenz system can fully realize the drive response synchronization. The simulation results are shown in Figure 3. The abscissa represents the transmitter signal x(n) and the ordinate is the signal at the receiver. x'(n), as can be seen from the figure, the two are strictly synchronized.
4 Matlab simulation results and analysis
4.1 Simulation results
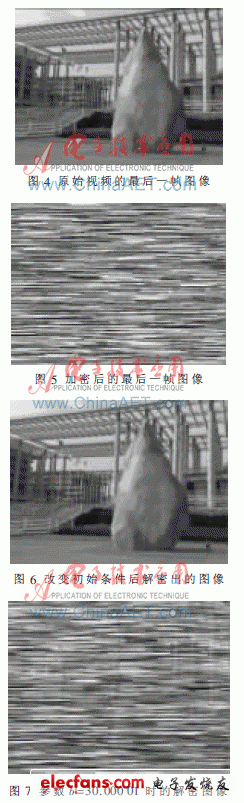
Under the working platform of Matlab7.1, according to the encryption scheme proposed above, the corresponding program is used to encrypt and decrypt the video file "original.avi". The initial value of the Lorenz system (x0, y0, z0) is taken as (0.01). 0.02, 0.03), Fig. 4 to Fig. 7 are experimental results of encryption and decryption, wherein Fig. 4 shows the original image of the last frame in the original video, and Fig. 5 is an effect diagram of the original image of the last frame after being encrypted by the chaotic system. Figure 6 is an image rendering of the decrypted image when the system parameters are completely consistent and the initial conditions (x1, y1, z1) are changed to (10, 20, 10), and Figure 7 is modified after the system parameter b is 30.000 01. The effect map.
 4.2 Analysis of results
4.2 Analysis of results After adopting the above encryption algorithm, the "original.avi" is simulated by Matlab simulation tool programming. It can be found that since it is video encryption, only a single frame image can be analyzed, as shown in Figure 5, it is encrypted. After the image of the last frame, the encryption effect is quite good, and the content of the video file is completely invisible. When the initial conditions (x0, y0, z0) of the Lorenz chaotic system are different and the system parameters (a, b, c) are completely matched, the image of the last frame obtained is decrypted as shown in Fig. 6, complete and original image. The same, the decryption effect is very obvious. Then, adjust the system parameter b, and re-take the value of b to 30.000 01, and get the decryption effect diagram shown in Figure 7. The decrypted image can not be seen clearly, very fuzzy, which means that the encryption algorithm has very With high security, the security of the system is mainly due to the high sensitivity of parameter mismatch between the sender and the receiver.
According to the above simulation results and analysis, chaos itself has many advantages in implementing passwords, and its inherent deterministic randomness and low computational complexity have great appeal. At present, domestic and foreign scholars have applied chaotic encryption theory to video encryption, mainly focusing on direct encryption. They do not take advantage of the characteristics of video data and the advantages of selective encryption. They do not combine well with video compression standards. Therefore, it is difficult to improve its practicality and real-time. Combining chaotic encryption with selective encryption is an important development direction for chaotic security algorithms in the future.
Light emitting diode (LED) light therapy is growing in popularity in both aesthetician offices and at home. Using varying LED wavelengths, this skincare technique purportedly helps treat acne, reduce inflammation, and promote anti-aging effects.
You may be a candidate for LED light therapy if you have these types of skincare concerns and haven`t gotten the results you want from over-the-counter (OTC) skin products. LED therapy is also safe for all skin colors, and it doesn`t cause any burning.
But there are a few catches. For one, LED therapy can be expensive, and the results aren`t guaranteed. It`s also not safe if you take certain medications or have an active skin disorder.
Talk to your dermatologist about your skincare concerns and whether LED light therapy is a viable option for you.
therapy lamp, light therapy lamp, phototherapy light
Shenzhen Ri Yue Guang Hua Technology Co., Ltd. , https://www.ledlightinside.com