Although Ethernet has been invented for more than 40 years, it still has a major impact on almost every aspect of network and communication systems. Originally a simple, low-cost local area network (LAN) technology, Ethernet is now widely used in most wide area networks (WANs) responsible for providing global telecommunications, wireless and Internet services. The low cost and high performance of Ethernet has also made it a popular medium for many emerging applications, such as storage area networks and video transmission applications. Next, Ethernet will also play an important role in the emerging Internet of Things (IoT).
Ethernet epic
Ethernet was originally developed in 1973 by Xerox's legendary PARC Research Laboratory, which uses a shared coaxial cable to transmit packet-based messages between two computers at 1 Mbit/s ( figure 1). Over the next 30 years, Ethernet has undergone several revolutionary changes that allow it to communicate using a variety of other types of copper and fiber media. The development of these new media plus transceiver technology has led to a significant increase in channel capacity and a significant reduction in deployment costs.
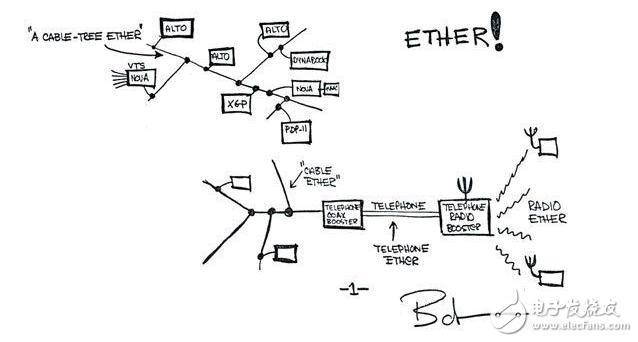
Figure 1: Ethernet originally invented by Bob Metcalfe in 1972. (Photo courtesy of Xerox's PARC)
By the end of the 20th century, the leaders of the Ethernet standard, the Metro Ethernet Forum (MEF) and the IEEE 802.3 committee, had begun a series of improvements, hoping that Ethernet could work seamlessly across the WAN. Today, Ethernet has become the medium of choice for almost everybody, from carriers and businesses to residential customers.
Accelerating the spread of IP-based (Internet Protocol)-based Ethernet infrastructure is one of two major trends in the communications industry: moving from fixed wired connections to wireless networks, and to "all services (XaaS)", also known as The steady growth in demand for cloud services.
Mobile and cloud network services are mainly due to the exponential growth in the size of global IP services. According to Cisco's forecast, global IP service capacity will reach 1.4ZB (1 billion TB) by 2017. Ethernet provides the most cost-effective and scalable way to meet the demands of mobile backhaul and cloud services.
But the shift of Ethernet from LAN to WAN and data center is just the latest advancement in the technology's near-global penetration goals. In the near future, its versatility and low cost advantages will make it the most convenient upgrade path for most non-standard legacy protocols that are still popular in many industrial, utility, transportation and government networks.
The Internet of Things is a term recently coined to describe machine-to-machine (M2M) networks that support the free exchange of messages between so-called "smart objects" and applications that depend on them in commercial, industrial, and civil organizations. Although the Internet of Things is still in its infancy, it can provide real-time visibility and control of real-world objects such as water meters and electricity meters, point-of-sale terminals and traffic lights, and thus may bring unprecedented efficiency and transparency to almost every aspect of our lives.
According to Morgan Stanley, 75 billion devices will be connected to the Internet of Things by 2020. Unsurprisingly, Ethernet will once again evolve into the foundation of the Internet of Things.
To meet the demands of mobile, cloud and IoT networks, Ethernet technology must acquire new features that its founders never thought of. While Ethernet was initially over-powered for LAN applications, the new services that Ethernet is expected to offer and the challenges it will face will require its next generation to provide native support for three key functions: determining xing service offerings, Precise timing and synchronization, as well as security.
Reliability and deterministic performance
Most IT and telecom analysts believe that the fundamental reason for the massive shift of traditional enterprise IT networks to the cloud is the recent sharp rise in the demand curve for high-bandwidth, reliable, and secure access to XaaS. The Cisco Global Cloud Index for the third year, released in October 2013, predicts that global cloud business will grow 4.5 times from 2012 to 2017 (composite annual growth rate of 35%). In addition, a survey conducted by Forrester ConsulTIng in September 2013 showed that more than 75% of companies are currently using or planning to use certain cloud services.
It's not well understood that the steadily shifting WAN to Ethernet infrastructure has recently contributed to the explosion of cloud service availability and adoption. In fact, the capital, deployment, and operational costs of an Ethernet network are only a small fraction of the traditional TDM (Time Division Multiplexing) systems that it replaces.
Service Providers (SPs) also saw significant revenue growth due to the provision of Ethernet-based access, transportation and WAN services. For example, according to the US Carrier Ethernet Service 2013-2017 forecast published by International Data Corporation (IDE), the total revenue of Ethernet services in the United States alone will increase from $6.2 billion in 2013 to $10.1 billion in 2016. .
Although the packet-based WAN has been steadily replacing the frame-based SONET/SDH system for more than a decade, the main boost for the widespread adoption of Ethernet services comes from the actions of the Metropolitan Area Network Forum (MEF) leaders. Ethernet is needed to meet the additional attributes expected by users and is standardized. The addition of these new attributes, such as standardized services, Operations Management and Maintenance (OAM) capabilities, Quality of Service (QoS) classification, and reliability requirements, has driven the development of standard Ethernet into Carrier Ethernet.
Founded in 2001, MEF is a global industry consortium of telecommunications service providers, cable multi-system operators (MSOs), network equipment/software manufacturers, semiconductor suppliers and test organizations. It first defined Carrier Ethernet, now known as CE 1.0, which pioneered the first generation of standardized carrier-grade services. CE 1.0 builds a solid foundation on which Carrier Ethernet can evolve and deliver standardized Ethernet services over a single provider network.
In January 2012, after Ethernet became the ubiquitous WAN foundation, MEF defined a new generation of Carrier Ethernet: CE 2.0. CE 2.0 provides globally differentiated applications on interconnected and managed networks. The biggest difference between CE 2.0 and CE 1.0 is its specification for multi-service categories (mulTI-CoS) and its interconnection and manageability standards (see Table 1).
Table 1: Evolution of Ethernet.
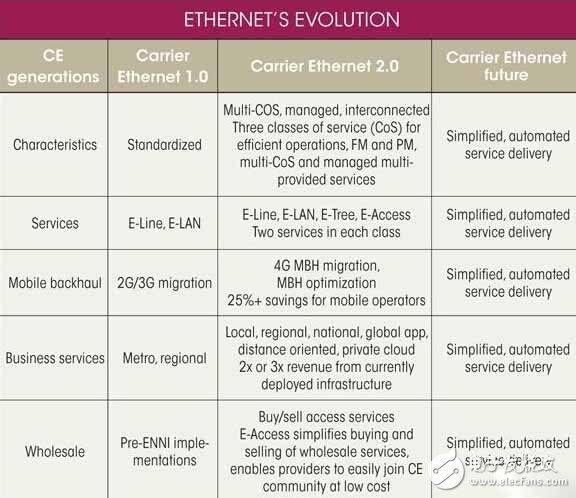
These standards are especially important in today's Ethernet market because each company relies on a specific, unique set of network services. Businesses don't need any surprises about their network performance, nor can they afford any difference in the behavior of their service level agreements (SLAs) at different locations. CE 2.0 ensures that companies enjoy consistent, stable service reliability across their entire network.
The ability of a service provider to monitor the connectivity and performance of any given service provided to a customer is a good example of these new features. The use of inbound maintenance endpoint (MEP) OAM technology allows service providers to remotely monitor service performance up to the customer's location. This greatly improves the ability to detect and locate faults, thereby reducing on-site service and operating expenses; and truly enabling carrier-grade services. It also supports the high-margin, low-loss and low-latency services needed in the enterprise, financial and mobile backhaul markets.
In addition, service providers must work more with multiple network operators to expand the scale and scope of their Carrier Ethernet service offerings. Multi-operator services are especially common in mobile backhaul and global enterprise services. With inbound MEP OAM technology, service providers can monitor end-to-end connectivity health and performance, as well as concurrent monitoring across each carrier's network.
A recent announcement by Carrier Energy's service provider, Masergy CommunicaTIons, further underscores the growing importance of Carrier Ethernet for cloud services. In this example, Amazon chose Masergy to provide direct private access to Amazon Web Services (AWS) throughout North America, addressing the challenges of non-deterministic performance, reduced security, and lack of QoS capabilities associated with public Internet access.
As more and more enterprises turn to cloud services, service providers can deploy cloud-enabled services with cost-effective and high-performance CE 2.0-compliant devices. In fact, a new generation of Ethernet access devices has adopted hardware-based CE 2.0, enabling higher performance, lower cost power and smaller service providers looking to provide these demanding, high-performance cloud network services. Size solution.
Timing and synchronization are key
Mobile networks require precise timing—for example, to support call handoff between base stations—and a stable reference clock for generating radio frequency frames for data transmission between the cellular base station and the user. For 2G/3G networks, timing is typically provided by SONET/SDH-based T1/E1 lines or by GPS satellites.
But in order to support the exponential increase in bandwidth demand without a proportional increase in capital expenditures (CAPEX), operators have quickly moved to packet-based Ethernet backhaul networks. The timing scheme provided by SONET/SDH is not only expensive, but also not good enough for TD-LTE (time domain) and LTE-Advanced (LTE-A) wireless networks, because SONET/SDH can only provide frequency synchronization and cannot provide necessary Phase synchronization. This is why we see the urgent need for the IEEE 1588v2 Precision Time Protocol (1588 or PTP). This protocol uses a packet-based synchronization mechanism that provides both phase and frequency information with the accuracy required by advanced wireless networks.
Initially, the low cost and superior performance of 1588-based Ethernet made it a popular way for wireless carriers to upgrade their existing T1/T3 backhaul networks. Recently, Ethernet's 1588 function has become an invaluable asset, allowing operators to deploy microcells and femtocells to provide more capacity for urban corridors and indoor environments (Figure 2).
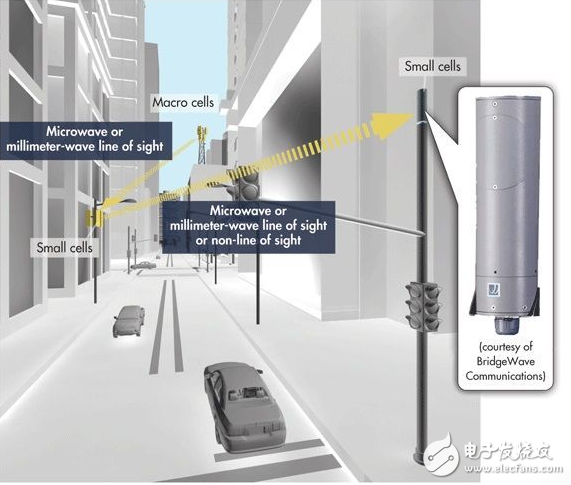
Figure 2: Mobile operators use microcell/picocell clusters and Ethernet backhaul infrastructure to enhance the capacity and coverage of their 4G/LTE services.
Since many of these small cells are located in locations where GPS signals cannot be received, GPS signals cannot be used to maintain synchronization with other wireless nodes as usual, and they typically use IEEE 1588 Precision Time Protocol (PTP) over their Ethernet backhaul links. Obtain the necessary timing information.
Almost all mobile base stations rely on GPS/GNSS satellite transmission to obtain a very important 1 pps signal, which is used to calculate the date and time (ToD) required for the next second conversion and to synthesize the underlying source RF. In many environments where these so-called small cell nodes are present, the node cannot reliably access legacy GPS signals for providing the high precision frequency and ToD synchronization information required for TD-LTE and LTE-A networks. If a unified time domain cannot be maintained on the network, the call will be disconnected, messages will not be sent, and overall Quality of Experience (QoE) will drop.
1588 can solve this problem by sending timing information in a dedicated packet and using a second mechanism to manage packet delay variation (PDV), which is the small but inevitable time variation of the 1588 packet passing through the network. The recovery time therefore has errors. Each mobile technology defines a minimum level of frequency and phase error that can be tolerated, which defines the maximum time error that the backhaul network can introduce, and further limits the ability of each network element or overall network device to introduce 1588 packets. difference.
Therefore, operators need to carefully design their networks and consider the maximum error that each node and different media (such as fiber and microwave links) can introduce in the 1588 packet path. For ease of processing, the International Telecommunication Union Telecommunication Standardization Sector (ITU-T) is standardizing different device classes, corresponding to different maximum time error levels in the 20ns to 50ns range. Available silicon chip solutions enable network equipment designs to meet these budget requirements. Among these solutions, at least Vitesse's VeriTIme chipset solution uses a compensation mechanism that can maintain the 1588 timing domain even on a well-changing microwave link.
1588 will also play an important role in many other next-generation network applications, including wired IoT networks. Originally developed to support high-precision timing in industrial automation systems, the 1588 now offers real-world/real-time applications with accurate ToD information, timestamp input, scheduled output, and simultaneous output.
By eliminating many of the so-called "response time jitter" that would limit the performance of traditional control networks, the 1588 can even support a particularly large, widely distributed cluster of intelligent objects to complete time-critical real-world tasks, ranging from managing smart utility grids. Go to the driverless car on public roads.
For example, in a smart grid, utility companies can use 1588 to stabilize their grids as needed to prevent sudden spikes. How is this done? The approach is to provide real-time load data and provide the ability to quickly control load shedding systems already deployed in residential, commercial, and industrial buildings (Figure 3). The 1588-based smart grid also helps utility companies manage distributed energy sources such as rooftop photovoltaic systems. Similarly, in a driverless car system, the 1588 ensures that the road gets the real-time traffic and congestion data it needs, and the commands generated are fast enough to reach the car on the road, resulting in smooth traffic.
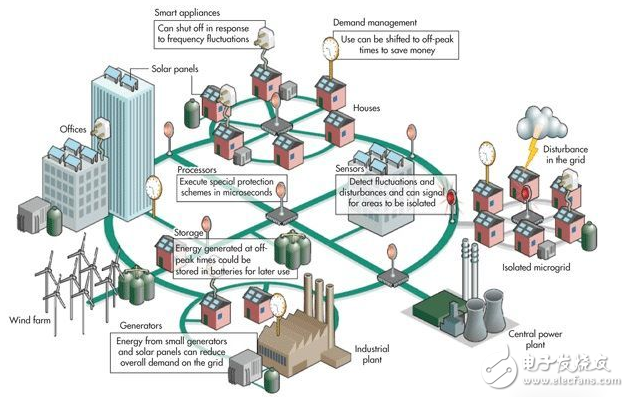
Figure 3: Ethernet will be at the heart of the Internet of Things (IoT) infrastructure, bringing intelligent and real-time control to many large, highly distributed systems such as cellular networks, driverless car systems and smart grids. (provided by SmartGRidTech)
In particular, commercial silicon solutions that support 1588 timing functions are available on the market today. These solutions not only meet stringent accuracy requirements, but also meet the stringent requirements of the small size and extended temperature range proposed by the IoT environment.
Safety is very important
At the beginning of Ethernet, the number of computers was very small and the price was very expensive. Most computers were limited to companies, governments and academic groups. In many cases, the only protection for a computer is a simple login password. Although there are no more security measures than simple passwords, these computers were considered quite secure at the time because they were physically isolated from the "real world" and few had the technical expertise necessary to access them, and There are few things that are of interest to outsiders on the Internet.
But in fact, even in the early days, these assumptions may be incorrect, and it is certain that as long as the network begins to touch the real world, these small security measures are not much different from undefended.
Today, security information, computing infrastructure, and the networks that connect them have become the focus of everyday discussions, with reports of malware, identity theft, intellectual property theft, and denial-of-service attacks on business and government network infrastructure almost every day. To address these challenges, the industry has implemented multiple network and data security models, including:
* Front End Authentication, Authorization and Billing (AAA)
* Confidentiality, generally solved by encryption
* Data integrity to ensure that data has not been tampered with
* Usability, usually targeting denial of service attacks
*Physical security, building access and vandalism
The following discussion focuses on encryption because it provides the most efficient way to secure network links and is particularly well-suited for enterprise use of cloud services or data center interconnects. In addition, many government regulations involving health care and finance, including HIPAA, PCI, Sarbanes-Oxley, Basel-II, and food and drug management, require all data to be encrypted before leaving the physical security of the building.
Concerns about the security of mobile backhaul networks are also increasing, including: multiple operators share backhaul infrastructure, geographically distant cellular tower deployment, and outdoor small cells lack physical security. The most commonly used network security protocol at the moment is IPsec, which works at Layer 3 (L3) in the IP hierarchy. Although IPsec works well in a routed network, it is expensive to implement because it typically requires a dedicated standalone or embedded encryption engine.
The IEEE 802.1AE "MACsec" security standard and its configured key management protocol 802.1af (also known as KeySec) provide an alternative to working in the second layer (L2) of the Internet Protocol (IP) hierarchy. . Although MACsec/802.1X does not seem to be very popular (mainly used in data centers), its L2 operation makes it simpler, cheaper, easier to use, more efficient, and easy to scale. For a growing number of service providers offering MEF CE 2.0 services and MPLS (Multiprotocol Label Switching)-based L2 Virtual Private Networks (VPNs) and other Carrier Ethernet L2 VPN services, this is a A very cost effective solution.
When we consider the encryption scheme for mobile backhaul links, we need to consider the strict timing requirements discussed earlier. Although there is no industry-wide definition of "safe 1588", there are solutions available, the most famous being the Intellisec-based devices offered by Vitesse. They are suitable for Gigabit and 10 Gigabit Ethernet links and provide wire-speed encryption performance without sacrificing timing accuracy. These solutions provide a common encryption solution for confidential communications over Ethernet networks and any MEF CE 2.0 Ethernet or MPLS service provider connection.
The Internet of Things, like enterprise and carrier-grade networks, requires powerful encryption to secure many access points on the network. As more and more machines become smarter and require network connectivity, Ethernet or "industrial Ethernet" for IoT (widely encompassing industrial process control, energy distribution, automotive and even public transportation) has expanded rapidly.
In IoT applications, the network was once characterized by proprietary communications and network protocols. However, higher bandwidth and higher network requirements in IoT applications make Ethernet a must-have technology. While still containing only a small number of industrial connections, Ethernet is rapidly expanding in this area, driven largely by smart grid energy distribution, transportation and automotive applications. Any of these networked devices with IP addresses can theoretically be compromised. The more “things†that are connected to the Internet, the more information a third party can access.
Trustwave Holdings researchers David Bryan and Daniel Crowley have invaded many connected devices, and they believe that security is often overlooked during product development. As many as 75 billion IoT connections will be inclusive, ranging from traditional industrial connections (such as factory networks) to personal home appliances. All of these extra connections, along with the small cells in the backhaul network, will add access points to the hacker. With the development of the Internet of Things and the increasing number of connected devices in the world, scalable, cost-effective security technologies will only become more important.
Although with the rapid spread of Ethernet connectivity, end-to-end MACsec encryption will grow significantly in the next few years, but it must not affect another important aspect of the IoT network: timing and synchronization. As mentioned earlier, OEMs need to use the latest security technologies that support both high-precision network synchronization and wire-speed encryption.
Neckband Earphones,Neck Earphones,Best Neckband Earphones,Wireless Neckband Earphones
Dongguang Vowsound Electronics Co., Ltd. , https://www.vowsound.com