Virtualization technology shifts the business value of network services from the services provided by dedicated hardware devices to the services provided by software. Internet companies are the beneficiaries of virtualization technology. Their business development and operations have gone from the physical servers that rent traditional IDC data centers to the IaaS (Infrastructure as a Service) that is virtualized in computing, storage, and DC intranets. stage. Further, it will evolve to the PaaS (Platform as a Service) phase of integrated development and operation. At this time, business iterations and online speeds will be faster, and the ecosystem of integration partners will be stronger.
Traditional operators currently operate voice, IPTV, high-speed Internet, and enterprise VPN services through private APIs (application programming interfaces) or network management interfaces provided by dedicated devices; their own IT systems, such as B/OSS, are mostly It is also running on the physical server of IDC with a low degree of intensification.
The needs of end users are changeable and personalized, and Internet companies have introduced a large number of connections into the cloud with the lead in virtualization, and these connections have created value for Internet companies. The value of the carrier's proprietary voice and IPTV services is weakened by the OTT business. Carrier pipeline traffic and connections grew rapidly, but revenue did not increase significantly.
The backwardness in the virtualization process has made operators disadvantaged in the commercial value of Internet services. Even if operators want to achieve a win-win situation with Internet companies, operators' responsiveness needs to keep pace with the changes in Internet companies and end-user businesses. Accelerating the process of network virtualization is an urgent task for operators.
CO refactoring to enhance virtualization capabilities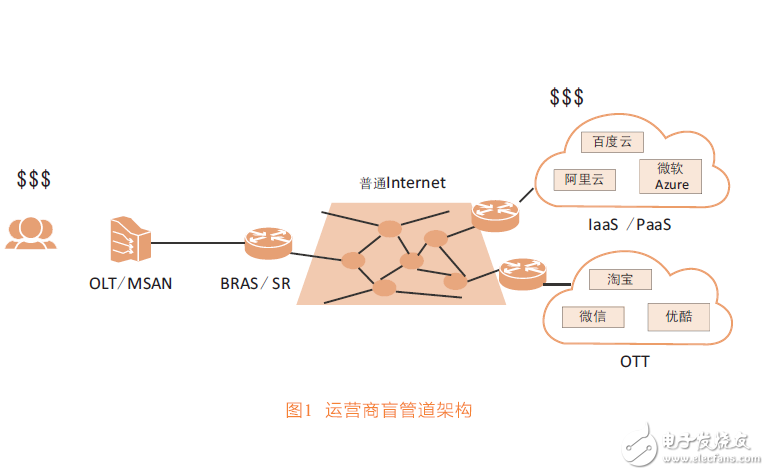
In the face of challenges, operators have two choices, either as a simple blind pipe or as an intelligent pipeline that moves on demand. The blind pipe architecture is shown in Figure 1. The operator can only get the income of the universal Internet connection. In a blind pipeline, operators cannot predict changes in user experience requirements and cannot meet the needs of network on-demand customization. For example, most of the time, the “best effort†pipeline can meet the needs of Internet access, but occasionally when turning to video sites, Need to increase bandwidth; most of the time video sites push videos to users through unicast, but in some major events, customizing a multicast network can ensure the user experience.
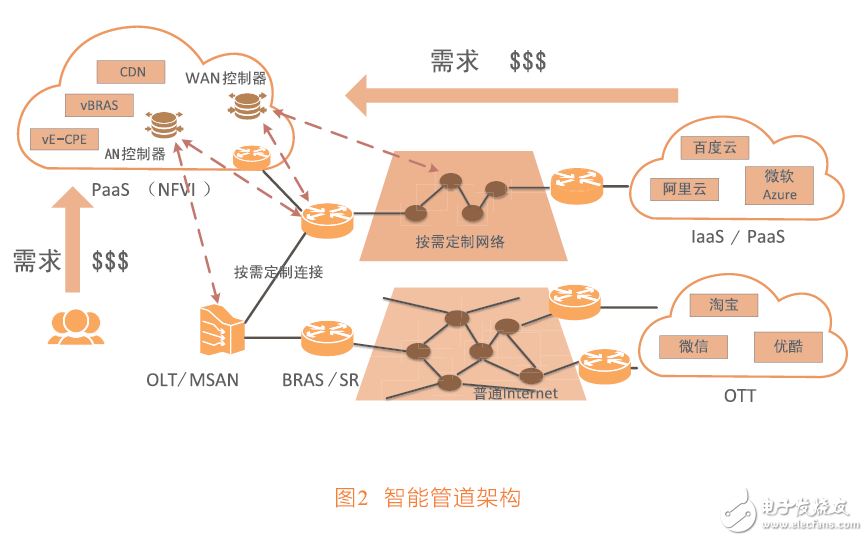
The intelligent pipeline architecture is shown in Figure 2. To gain more value, operators need to build a fast-paced network with PaaS as the core to meet the challenge. The current mainstream infrastructure operators have accepted the NFV network function virtualization concept proposed by ETSI, and plan to build a clouded data center as NFVI (NFV infrastructure). The data center based on the PaaS platform can be analogized to the service area along the expressway. Based on this, the operator can provide differentiated services for various traffic at any time.
A wide range of physical networks from access to the IP WAN are abstractly virtualized into the PaaS data center, creating a mirror of the actual network resources in the virtual environment. This allows network resources and functions to be programmed in a pure software virtual environment.
Internet companies and end users do not own the actual WAN physical network, and usually only use the Internet that provides universal service as a connection. If operators establish the ability to network virtualization, when valuable connections are about to take place, users and Internet companies can propose network customization requirements to operators, obtain shorter delays than Internet connections, or have more bandwidth and cost. Low one-to-many connection.
SDN technology helps in the implementation of virtualization. The control and forwarding separation of the SDN technology helps the software function to be separated from the dedicated hardware. Even physical network resources distributed outside the data center can be mirrored in the virtualized software world for use by VNF through the SDN controller. This is different from the traditional VPN private network. A traditional VPN cannot provide a virtualized image for itself, and does not provide a global network view for upper-layer applications. The network under SDN control can provide a global image of the network for upper-layer applications, allowing upper-layer applications to customize their own network connections.
Main components of access network virtualizationThe virtualization of the access network mainly includes two aspects: network virtualization and network function virtualization. Network virtualization: Implementing the slicing of the access network, each slice is a customized virtual network: it can be a pre-configured network with a long life cycle, such as a virtual access network that the basic operator wholesales to the virtual operator; It can also be a virtual network that is dynamically created and deleted according to user experience requirements. For example, when industrial control occurs, low latency and small bandwidth are required, and when VR occurs, low jitter and large bandwidth are required. Such network slices should be able to follow the changes in demand and quickly allocate matching network resources through the SDN controller. Through network slicing, the physical access network can be shared by multiple virtual access networks to achieve full utilization of resources without constructing an independent network for each usage scenario.
Network function virtualization: VNF, pure software function module, function development and verification does not depend on a dedicated hardware platform. The actual operation calculation and storage resources are taken from x86 and other virtualization platforms, and network resources can be taken from direct physics. Network connection, at this time, the traffic of the network needs to be imported into the function module; it can also be the image of the physical network obtained from the SDN, and the actual physical network is driven by the SDN, and the actual user traffic can pass through the VNF.
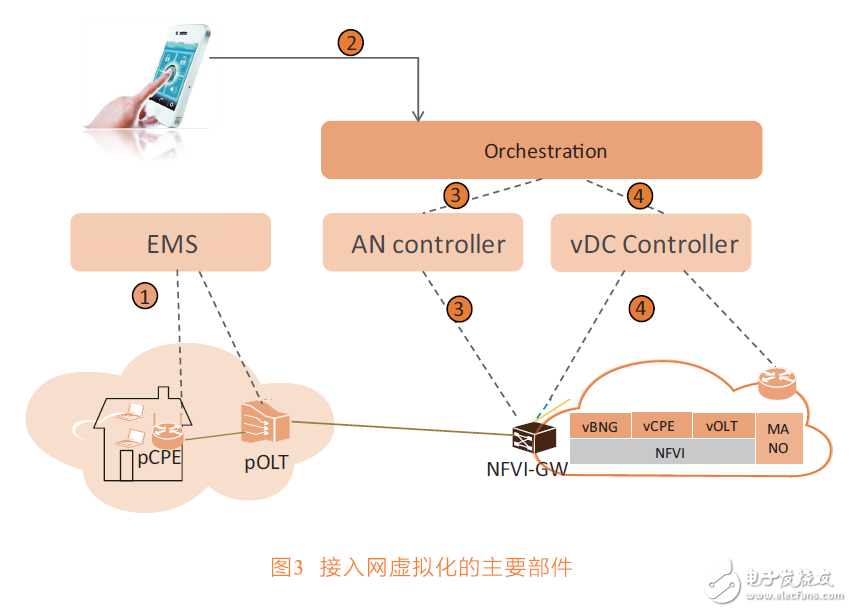
As shown in Figure 3, the main components of the access network virtualization include VNF (network function virtualization), NFVI platform, physical forwarding device (pOLT, various hardware gateways), access domain and DC domain SDN controller, and EMS network management. Wait.
The VNF components of the network function virtualization include vOLT, vBNG, vCPE, etc., and separate the software functions of the control plane and the management plane from the original physical OLT, BNG, and CPE.
The NFVI platform required for VNF operations is provided by the IaaS or PaaS platform, which performs physical computing, storage, and virtualization of network resources. Physical forwarding devices controlled by NFVI include distributed OLT forwarding devices, centralized NFVI-GW forwarding pools, and Overlay networks in data centers.
The SDN controller includes at least a vDC controller and an AN controller. Different from the case where the computing and storage resources are concentrated in the data center, the network resources are concentrated in the DC network of the data center, and many network nodes and links are outside the data center. The vDC controller virtualizes the Overlay network inside the data center. The AN controller virtualizes the user's access network to the NFVI. Various VNFs control the direction of network traffic through SDN controllers.
EMS configuration and virtualization-independent parts, such as actual physical nodes and links, are basically semi-permanent and generally do not change, and have little to do with the arrangement of upper-layer services.
In addition, when the access network is virtualized, it is also necessary to consider the relationship with the traditional network. For example, in cooperation with the traditional BNG, the following options are available, and the operator needs to consider it according to his own situation when deploying.
â—NFVI as an aid to traditional BNG
The IP session and user management are still completed by the BNG. The BNG offloads specific traffic in the IP session to the NFVI service chain to implement value-added services. Affected by the order of business processing, after the service chain such as vCPE is processed, it may need to reconnect to BNG from NFVI. Traditional BNG is not controlled by NFVI, so the traffic trend may be complicated.
â— NFVI diverts some users from BNG (recommended as a transition phase from BNG to vBNG)
The IP session and user management of the existing users or users who do not have the VNF service chain requirements are completed by the old BNG; the IP sessions and user management of the newly added users are completely imported into the NFVI, and the NFVI of this part of the users is completely controlled, such as vCPE and vBNG. The connections between the forwarding pools are controlled by the SDN controller.
â— NFVI completely replaces BNG with forwarding pool + vBNG (suitable for operators without traditional BNG and no PPPoE connection)
The access device OLT acts as a distributed physical forwarding pool to handle large traffic; the forwarding pools in various NFVIs can be assumed by the NFVI-GW or a dedicated hardware gateway, as a centralized physical forwarding pool in the data center. Forward various custom traffic that needs to initiate a VNF service chain.
With SDN and NFV technology, we are building a more agile, on-demand access network. The gradual maturity of data center technology is a large background for access network virtualization. The network's control and management functions can be virtualized by computing and storage resources without having to rely entirely on the limited capabilities of dedicated devices. SDN technology can help network virtualization scale out of the data center and out of the data center. Although more and more traffic will occur in east-west data centers or between data centers, a controlled access network is needed to distribute north-south traffic to data centers and traditional Internet as needed. Flexible use of various business software.
Lead Acid vs. Lithium: Safety
Safety is always a primary consideration when designing a solar system, but it becomes even more important when your system is on a boat far from shore, or an RV on a remote road. Different battery chemistries have different risk factors. Obviously, abusing any type of battery can create a dangerous situation. But with normal, and perhaps even a bit of rough treatment, the different batteries have different safety concerns that need to be addressed.
- Flooded lead acid batteries have an acid and water electrolyte in the battery that has to be checked on a regular basis. During normal charging cycles, this mixture turns into a gas that needs to be vented outside. A buildup of the gas inside a vehicle or vessel can be explosive. Proper ventilation mitigates this concern. The outgassing of the battery is normal, but requires owners to regularly check to see when the electrolyte level gets low from the outgassing. If low, it needs to have more distilled water added. This runs the risk of acid spills if overfilled or overcharged. This requires you to be prepared with proper safety equipment including gloves, safety glasses, and baking soda to neutralize the acid if needed.
- Sealed lead acid batteries do not have outgassing or electrolyte levels to check, as they do not outgas. Normal battery safety measures should be followed, like checking for tight cable connections, corrosion, and preventing physical damage to the battery itself.
- Lithium batteries also do not outgas, but certain types (the ones with cobalt, known as lithium cobalt oxide or LCO) can experience thermal runaway – a condition where the battery starts to get hot, which causes it to react to the heat and get hotter and hotter until it catches on fire. LCO batteries are most commonly used in cell phones, hoverboards, and electric cars, and are generally not recommended for mobile applications.
Storage Battery Pack,Power Pack Home,Battery Storage Pack,Battery Pack Storage
Shenzhen Sunbeam New Energy Co., Ltd , https://www.sunbeambattery.com